Threat Actor Profile: Qilin Ransomware Group

About
Qilin Ransomware group first appeared in the summer of 2022, first called ‘Agenda’ Ransomware and was written in Golang (Go). A user on the dark web was posting about the Ransomware and went by the name ‘Qilin’, fast forward to 2024 and the group goes by the name Qilin Ransomware. As well as changing their name, the group has also changed the language in which their ransomware is written in. The group’s ransomware is now written in the language Rust. This could be for many reasons, but researchers believe it’s because of the language’s capability to evade detection and the its ability to target Windows, Linux and VMware ESXi servers.
The threat actors are motivated by financial gain, targeting high value companies who are most likely to payout. The group has shown a medium level of activity consistently over the past months, listing several successful attacks per month, but there could also be more that they aren’t posting on their dark web page.
The group offers an affiliate scheme which offers other hackers the chance to utilize the ransomware platform for a cut of their successful ransoms. In this group’s case, successful payouts of $3 million or less the developers take a cut 20% (leaving 80% to the successful threat actor), successful payouts of more than $3 million the developers take a 15% cut (leaving 85% to the successful threat actor). The group and its affiliates operate a double extortion method, by exfiltrating as well as encrypting the data. This allows the threat actor to threaten the victim company by releasing their data to the public if no payment is made.

The ransomware group doesn’t have any links to any governments, but the ransomware does have rules for its affiliates that it can’t be deployed in CIS countries (such as Russia, Belarus, Armenia and more). The cyber security firm, Group IB, has also observed recruiters for Qilin advertising on underground forums in the Russia language. But there is no further evidence linking them to Russia, therefor the no links are confirmed.
Victimology
The group doesn’t appear to target any specific industry or country. But like mentioned above, they do choose high value companies, which in their eyes are more likely to pay out. The group doesn’t appear to have any other motivations other than making money.
According to a report written by Sectrio in the summer of 2023, the most targeted country is the United States. The group have also targeted countries such as the United Kingdom, Australia, France and Germany.
The group has had two major hacks in the news over the past couple of months, showing their ability to take down large organizations. The first is Yanfeng, an auto parts supplier based in China. The company has 57,000 employees and over 240 locations. They supply parts to the likes of, Chrysler, Dodge and Jeep. Many companies in the US became affected by this attack due to them not having the parts they needed from Yanfeng. The group also is believed to be behind the December 21st hack of the Court Services in Victoria Australia, potentially leaking recordings of hearing from November and December. Due to the sensitivity of this case, there hasn’t been much more information released on the matter at the time of writing.
Methodology
Because the group operates an affiliate program, the initial access methods for the delivery of the Ransomware can vary. The most commonly used method by the group and its affiliates are phishing emails that contain malicious links. This will then allow the attackers to gain access to the network and commence their attack.
In May 2023, Group-IB posted an article where they showed they had got access to the Qilin affiliates platform. They were then able to show how the ransomware is operated and what customization the platform offered. The platform was broken down into sections, the first section focused on the victim, the affiliates can configure the name of the company, ransom amount, wait time and more. The second section looks more towards configuring the ransomware itself, the affiliates can configure the ransom note, directories, files, extensions, that they want skipped, services that will be stopped, login credentials, mode of encryption and more.
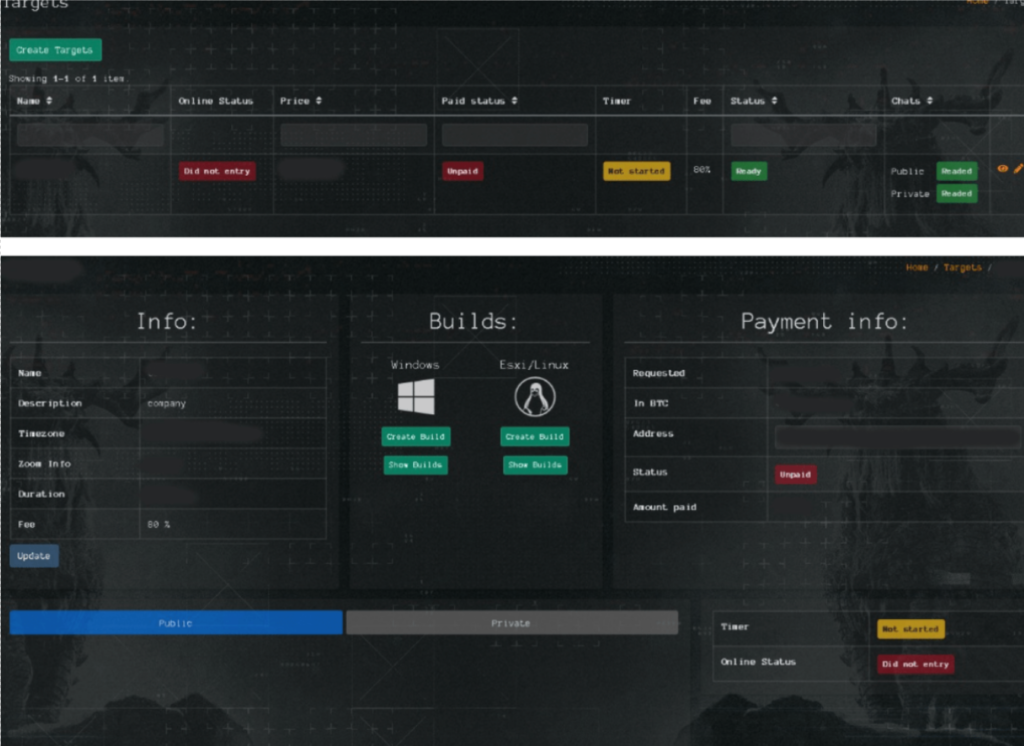
The remaining sections cover more admin side, covering blogs posts of victims, adding members of the team to the platform, news from Qilin, Payments and FAQs. As you can see from above, the ransomware has two types of builds: Windows or ESXi. Below I have laid out the groups TTPs in the MITRE ATT&CK Framework.
MITRE ATT&CK TTPs
Technique Name | Technique Code | Explanation |
Initial Access: Spear-phishing Link | T1566.002 | The group and its affiliates utilize phishing via link as their primary method of initial access. |
|
|
|
Defense Evasion: Process Injection | T1055 | The ransomware drops pwn.dll into the public folder. |
Defense Evasion: Dynamic-link Library Injection | T1055.001 | The ransomware drops injects the pwn.dll into svchost.exe. |
Defense Evasion: Safe Mode Boot | T1562.009 | The ransomware takes advantage of safe mode to avoid detection. |
| ||
Impact: Data Encrypted for Impact | T1486 | The ransomware encrypts for impact using AES-256 and the decryption key is generated in RSA-2048. |
Impact: Service Stop | T1489 | The attack will stop server specific processes making it harder for the victim to recover their data. |
Impact: System Shutdown/Reboot | T1529 | The attack will also attempt to reboot the systems in normal mode making it harder for the victim to recover their data. |
IOCs
SHA256:
76f860a0e238231c2ac262901ce447e83d840e16fca52018293c6cf611a6807e
Fd7cbadcfca84b38380cf57898d0de2adcdfb9c3d64d17f886e8c5903e416039
555964b2fed3cced4c75a383dd4b3cf02776dae224f4848dcc03510b1de4dbf4
37546b811e369547c8bd631fa4399730d3bdaff635e744d83632b74f44f56cf6
55e070a86b3ef2488d0e58f945f432aca494bfe65c9c4363d739649225efbbd1
E90bdaaf5f9ca900133b699f18e4062562148169b29cb4eb37a0577388c22527
References
https://www.sentinelone.com/anthology/agenda-qilin/
https://www.group-ib.com/blog/qilin-ransomware/
https://thehackernews.com/2023/05/inside-qilin-ransomware-affiliates-take.html
https://securityboulevard.com/2023/07/qilin-ransomware-report/
https://cybernews.com/news/qilin-ransom-payouts-undercover-sting/
https://www.ransomlook.io/group/qilin
https://courts.vic.gov.au/news/court-services-victoria-cyber-incident
https://sectrio.com/qilin-ransomware-report-2023/
https://cybernews.com/news/yanfeng-ransomware-attack-claimed-qilin/

